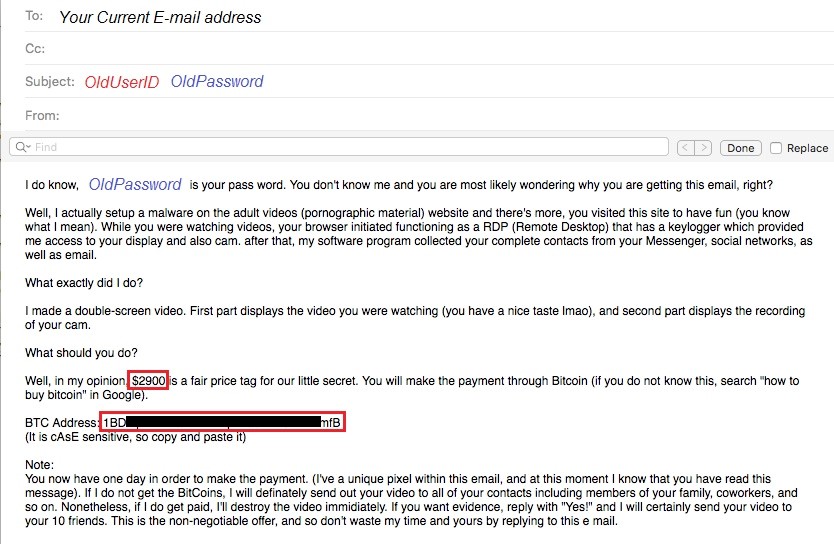
Prevent phishing and be alert
Scams regularly circulate us and target the University. Be extra vigilant and exercise safe practices:
- Carefully check all links before clicking them. When in doubt, ask someone around you.
- Be suspicious of emails that require you to enter your account and password.
- Remember that malicious attempts may come from uOttawa addresses that have been compromised.
- Be extra cautious of job offers requiring you to provide your personal information.
- Question emails that mention your account, such as it being terminated, requiring you to log in to continue, etc. These are typically fraudulent. Exit the email and contact the Service Desk independently to verify the authenticity of the notice.
We encourage you to continue to report suspicious emails by using the Report Message function in Outlook.